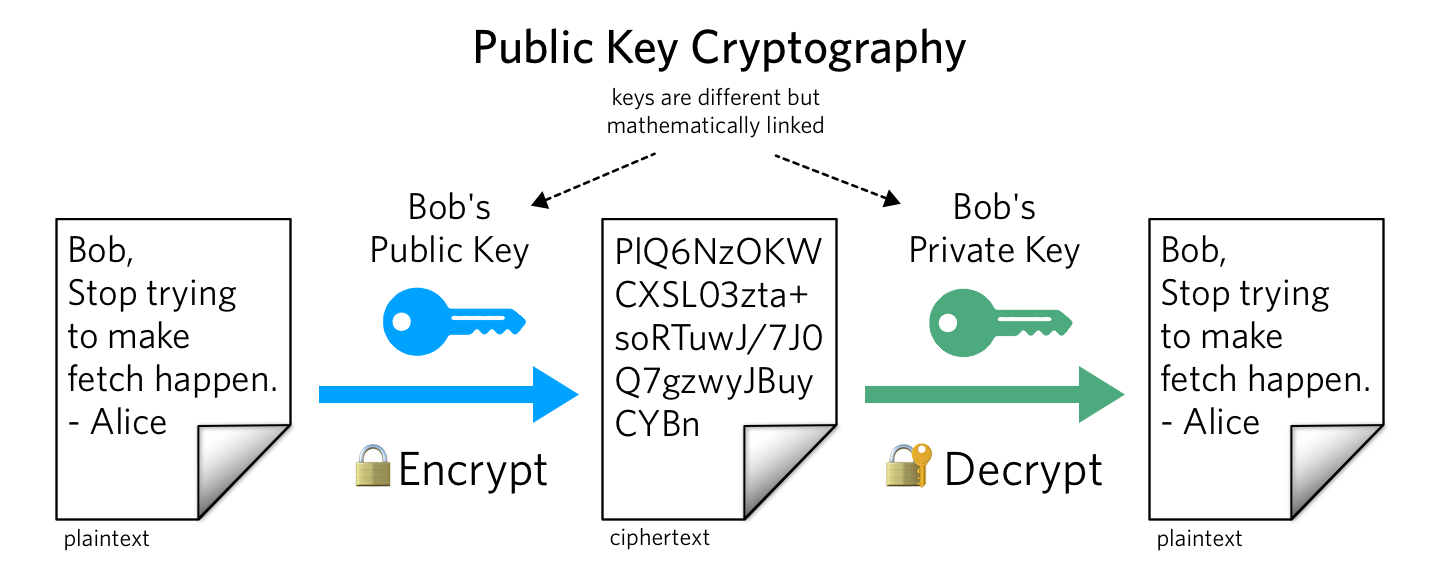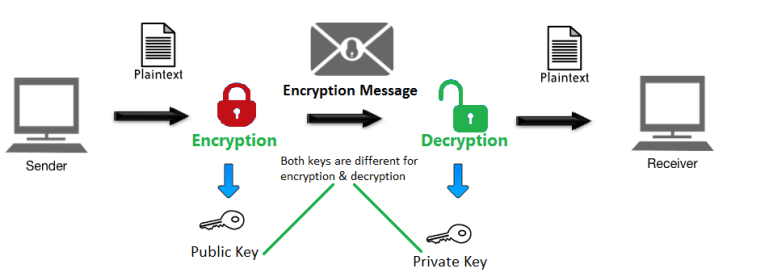
A Beginner's Guide: Private and Public Key Cryptography Deciphered | by Chris Coverdale | Coinmonks | Medium

A Beginner's Guide: Private and Public Key Cryptography Deciphered | by Chris Coverdale | Coinmonks | Medium
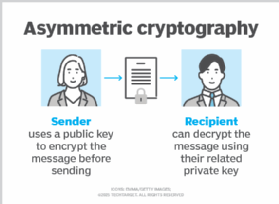
Generation/verification of public keys: The protocol with multifactor... | Download Scientific Diagram
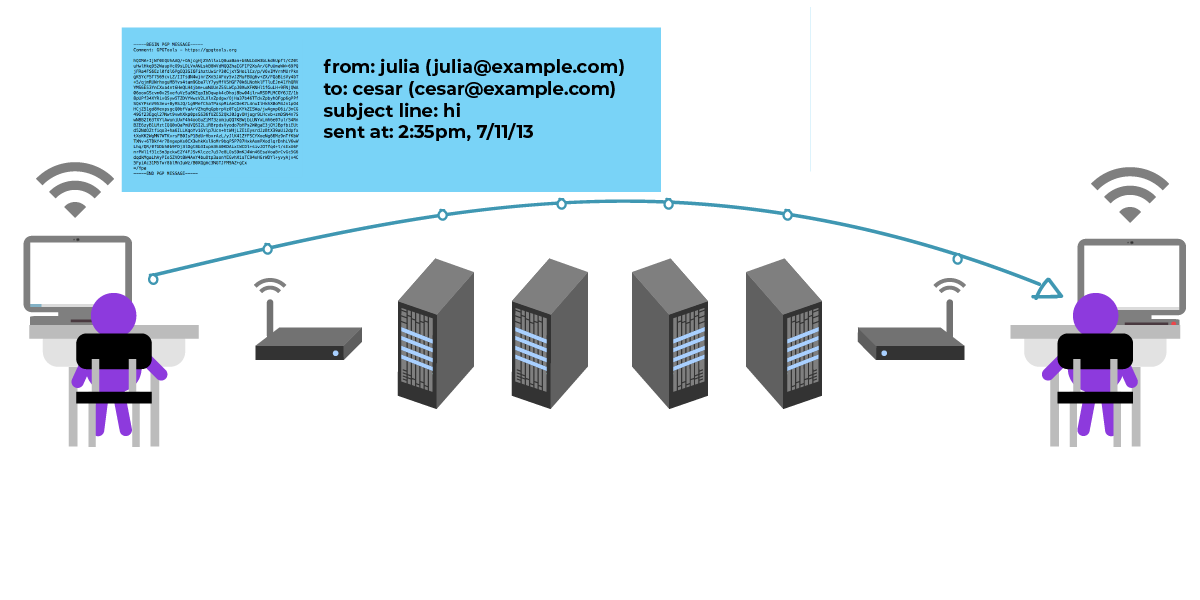
A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work? | Surveillance Self-Defense




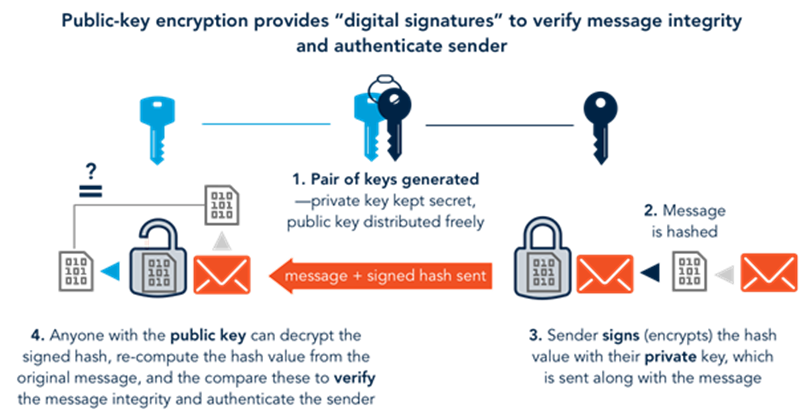


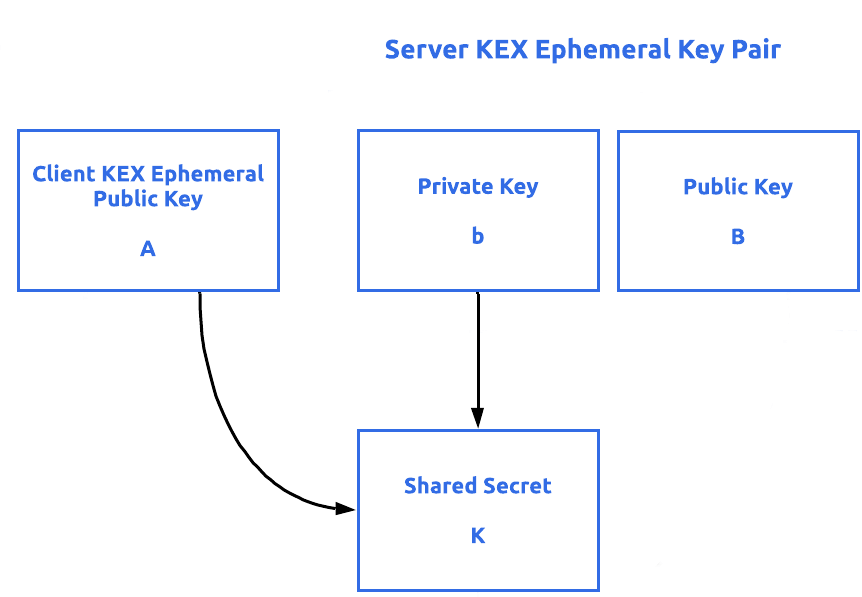
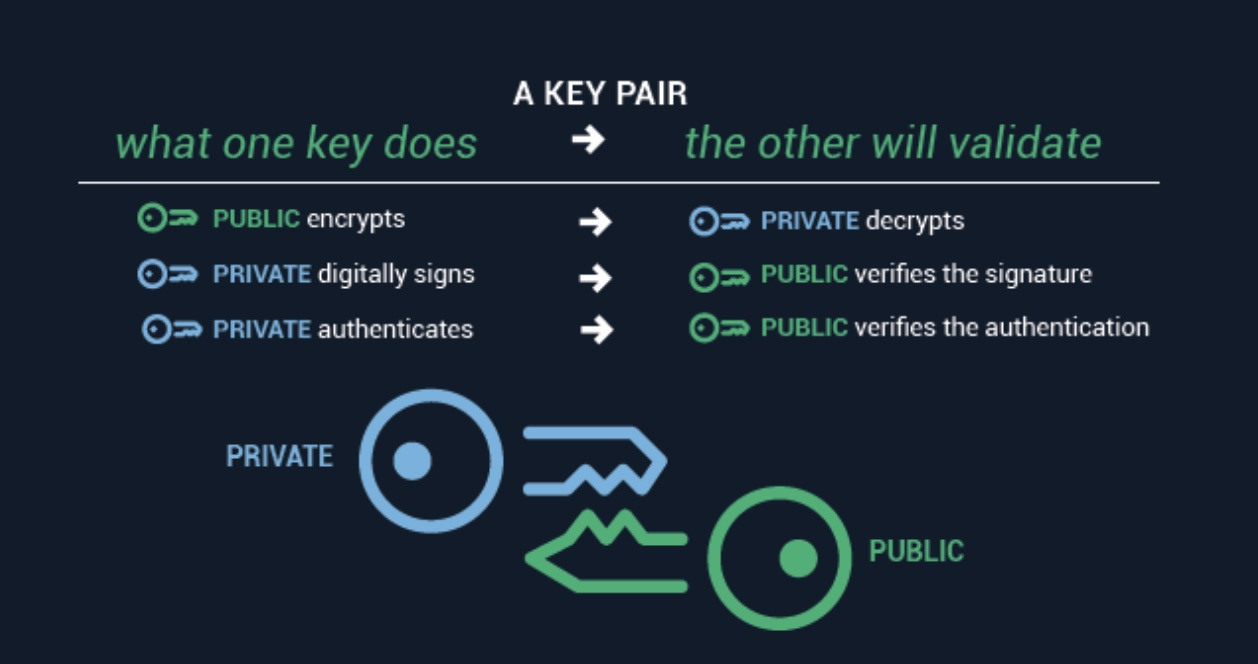
![4. Keys, Addresses - Mastering Bitcoin, 2nd Edition [Book] 4. Keys, Addresses - Mastering Bitcoin, 2nd Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781491954379/files/assets/mbc2_0405.png)